Cyber threats for gambling & gaming sector are rising
The UK has been at the forefront of the global gambling industry for nearly two decades, passing laws to regulate remote gaming as early as 2005 – and cyber threats for gambling and gaming are rising.
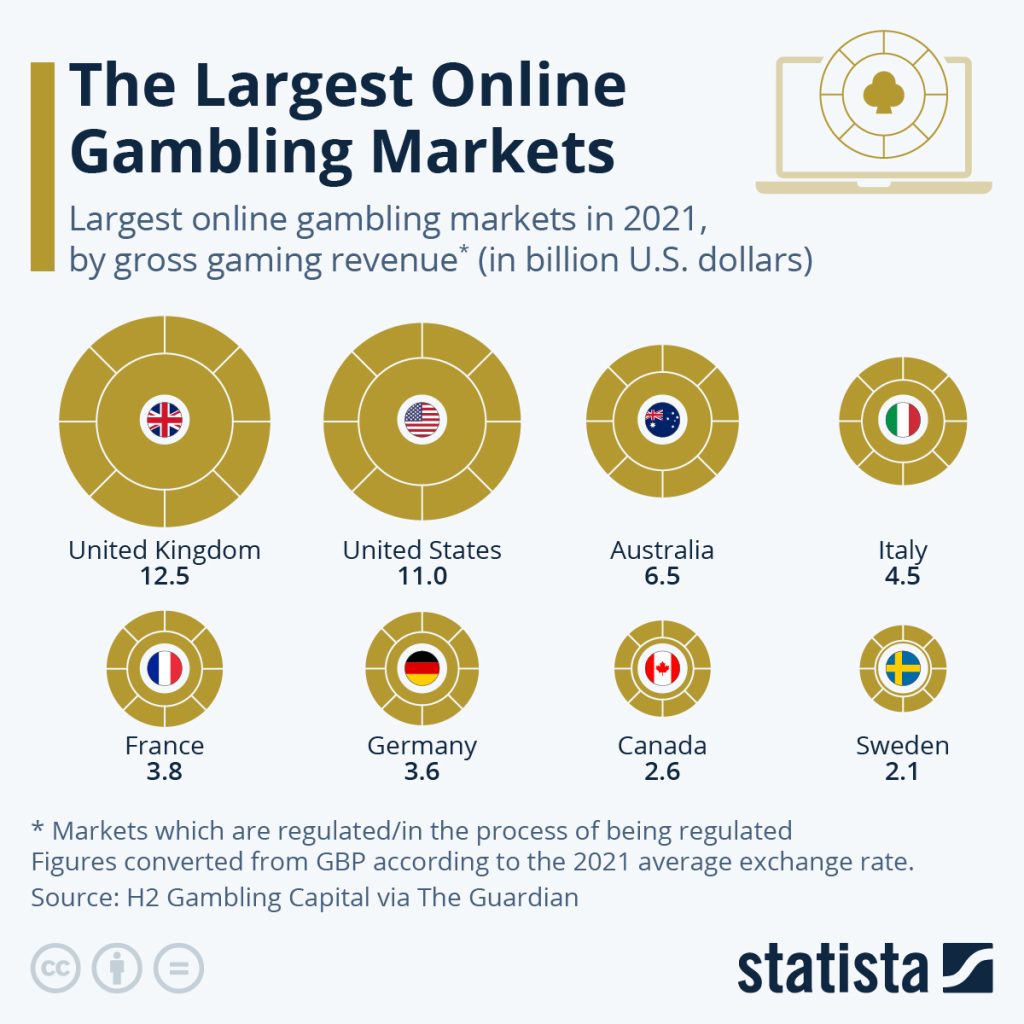
It also has the largest regulated online gambling market in the world, generating a total gross gambling yield (GGY) of £15.1 billion in the period between April 2022 and March 2023, making it an attractive target for criminals.
This is a 6.8 per cent increase on the previous year and a 6.6% increase on the last pre-lockdown period between April 2019 and March 2020.
SOURCE: https://www.statista.com/chart/29048/largest-regulated-online-gambling-markets
According to forecasts published by Technavio, this is poised to increase by $2.83 billion (£2.19 billion) by 2026, exhibiting a compound annual growth rate of 5.25%.
According to the UK’s National Cyber Security Centre (NCSC), the country’s gambling sector is worth more than £14 billion, employing more than 46,000 people and contributing £2.3 billion towards the UK GDP.
It’s estimated around 32% of UK adults are gambling weekly and an average 36.6 million active users are on web-based betting sites. Around £4.7 billion of the overall GGY comes from online platforms.
This presents an obvious target for cyber-criminals who are looking to not only steal money, but also to find customer data for further criminal enterprise and has seen cyber threats for gambling and gaming rising.
Cyber threats for gambling and gaming sectors
With such high volumes of money, as well as customer data, moving through the industry, gambling, online gaming and eSports has found itself the target of cyber-criminals.
The Department of Culture and Media Services 2020 Cyber Breaches survey reveals that the majority (55%) of UK gambling businesses suffered a cyber incident of some kind within the previous 12 months and the cyber threats for gambling and gaming are continuing to cause concern.
All of those affected reported hacking, or attempted hacking, with malicious users trying to either take down their websites, applications or online services. The second most common forms of attack were viruses, spyware, malware or staff receiving fraudulent emails attempting breaches.
NCSC commissioned Ipsos MORI to conduct a mixed-method study into cyber security practices within the gambling and lottery sector in the UK.
The 2021 Cyber and Gambling Cyber Security in the Gambling and Lottery Sector Report found stakeholders generally felt that cyber security was an important function and a high priority within the UK gambling and lottery sector.
However, some also felt that it wasn’t seen as important as commercial priorities, and having board-level involvement was seen as the key to instilling a more deep-rooted cyber security mindset.
It also found the perceived threat level from cyber-attacks to gambling and betting organisations was mixed; while the majority indicated their organisation had suffered some kind of cyber incident in the past 12 months, none of the attacks were seen as substantial.
Recent incidents mentioned by these organisations all involved low-level credential stuffing or privacy related incidents and distributed denial-of-service (DDoS) attacks that were part of mass campaigns.
But with between 75-100% of gambling businesses saying they used a large number of third parties in order to provide their services, this highlighted a potential vulnerability to supply chain attacks.
Some stakeholders felt that cyber security was still seen as part of IT rather than being integral to the overall success of the business.
There was a strong sense that attacks are constantly evolving and becoming more targeted – especially in regard to ransomware since the pandemic (see below):
“I don’t think the overall level of threat has changed. I think it’s moved on. I think it’s become more of a challenge to organisations that didn’t have the technical architecture and setup for remote working.
“We de-scoped what we did, so it wasn’t so much of a challenge for us. I think the general threat’s moved on, as it always does, regardless of the pandemic. I think ransomware attacks are more problematic now than they were 12 months ago for sure [..] other things have been pretty static.” – anonymous comment by a Cyber security lead, UK based gambling provider.
Ransomware threat groups are exploiting vulnerabilities in vendor-controlled remote access systems to intrude casino servers and initiate attacks according to the US’s FBI, which issued a private industry notification in November 2023.
The warning followed a pair of high-profile ransomware attacks on casino and hotel giants MGM Resorts and Caesars Entertainment, as well as an attack against Marina Bay Sands in Singapore in the latter half of last year.
The attacks exposed personal information and, in some cases, disrupted casino and hotel operations.
In the UK’s gambling and gaming sector, one key concern for the potential impact of a successful cyber-attack is around a loss of reputation.
“Had the attacks been successful, it would have impacted the reputation of the company. That would have had a substantial impact, where we’d have to pay some losses as a result of that.
In certain cases, we would have had to go out to customers, let them know that something had happened with the account, for instance. So, had the attacks been successful, it would have had a substantial impact on our organisation.” – Anonymous comment by a Cyber security lead, UK based betting and gambling provider.
Why is eSports and gaming at a higher risk of attack?
The eSports and gaming industry is an attractive target for cybercriminals for several reasons.
- It generates billions in revenue, making it a lucrative target for financial gain.
- The sheer scale of gamers globally provides a goldmine of personal information that can be exploited for identity theft and other malicious purposes.
- The high-profile nature of the industry makes it an appealing target for attackers looking to make a statement or gain notoriety.
- Gamers often use mods, cheat tools, or other third-party programs, which opens up potential vulnerabilities for hackers.
- There are huge financial stakes in eSports, with top-level players earning big money prizes. This gives gamers an incentive to leverage attacks, like DDoS, to ensure they beat their competition.
Cyber breaches within the sector
In March this year eSports aficionados were rocked when the North American Finals of Apex Legends was disrupted and then cancelled by Respawn and EA because of “the competitive integrity of this series being compromised”.
This involved someone giving the professional players hacks like aimbots (things to help them shoot more accurately) as they were playing in the event, effectively causing them to “cheat”.
It wasn’t clear what the extent of the breach was but there was concern that it wasn’t just someone messing with the players but that a larger security issue might be affecting the wider playerbase.
According to an article in Forbes: “This has led to a mass of complaints about Apex’s anti-cheat systems, which clearly failed in a massive way for this situation. But it also speaks to just how advanced cheats have become as this is a private lobby for pros playing in an esports final.”
It’s not the first time a games company has been hit by hackers. In 2001 CD Projekt Red, makers of Cyberpunk 2077, and the Witcher series, said hackers had accessed its internal network, digitally scrambled some of its data servers and tried to blackmail it.
In 2020, popular gaming company Ubisoft won a lawsuit against a group of attackers who sold software to conduct DDoS attacks on servers running Rainbow Six Siege games in order to disrupt matches and attempt to gain advantages.
Mitigating risk – what can you do?
Simply put, cybersecurity in the gambling, gaming and eSports industry is the same as in any sector – effective data protection should be helping your business, not inhibiting it.
Ransomware, phishing, DDoS (Distributed Denial of Service) attacks are the most common forms of attack within the sector and are made a higher risk due to the increased number of third-party service providers within the supply chain.
There are a range of mitigating options which can help to manage risks, and protect against cyber-attacks, including regular risk assessment, data protection, website protection, compliance reviews and using tools like Veracity Trust Network’s Web Threat Protection.
Its patented, AI-powered technology detects Automated Bot Attacks and Supply Chain Attacks (OWASP class 7-10 and 12-13) accurately, quickly and before they can cause you damage. It only requires a single script and doesn’t interfere with existing DDoS or WAF solutions.
Veracity Web Threat Protection is a powerful answer with an incredibly simple, 5-minute setup. Either set and forget to block the bots with peace of mind, or use its powerful intelligence tools to improve your performance, ROI and security.
Talk to us today: